Key Features to Look for in a Secure Web Gateway Solution
A secure web gateway (SWG) acts as a security checkpoint for all inline internet traffic, standing between users and the threats that try to enter or steal data. An ideal SWG solution combines URL filtering, malware and threat detection and prevention, application control for popular cloud-based apps, ShadowIT, and data loss prevention.
Authentication
What is a secure web gateway? A secure web gateway solution provides additional security for your organization’s network. It integrates with your existing endpoint and network security systems to extend your company’s security posture. For example, some gateways offer data loss prevention (DLP). This feature is similar to content filtering but works in reverse: it detects when confidential information leaves the organization’s network and redacts it to prevent breaches. DLP is a critical component of an SWG because it can protect sensitive information from being downloaded to personal devices and shared with outside parties.
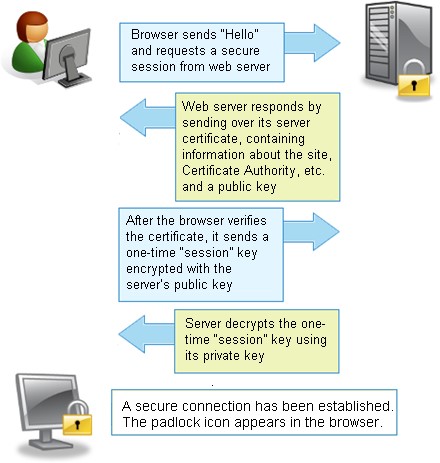
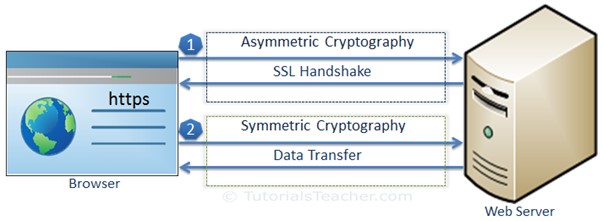
Additionally, some gateways have SSL/TLS decryption capabilities. This feature allows SWGs to analyze SSL-encrypted traffic and inspect incoming and outgoing data. This enables SWGs to prioritize alerts, ensuring that incidents that impact productivity or cause a potential threat are handled promptly and thoroughly. This also makes it easier for enterprises to manage and monitor SWG security operations. This is especially important since many of today’s workforces are remote and utilize unsecured endpoints on untrusted public networks to access corporate applications.
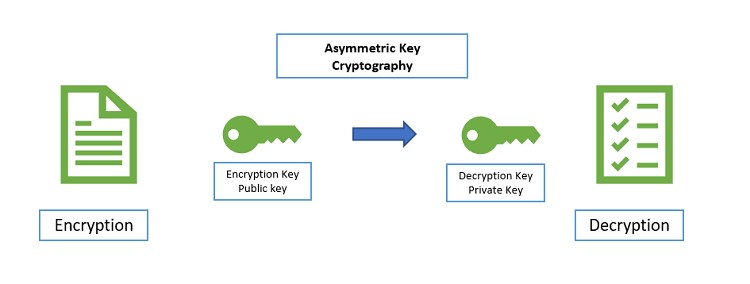
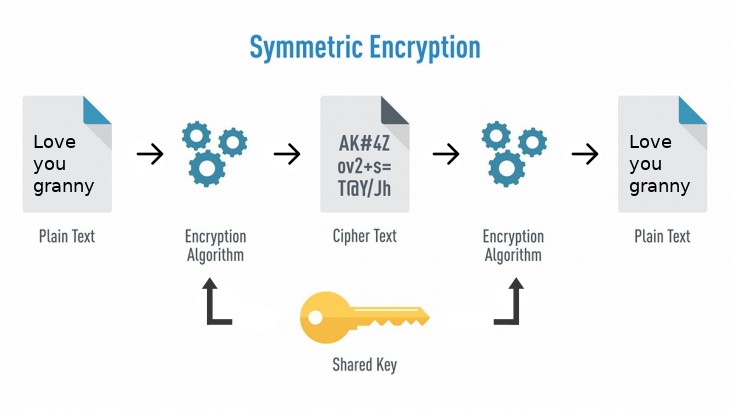
Encryption
With more organizations embracing remote work and cloud-based applications, their systems are at risk for malware attacks from outside the office. A SWG monitors web traffic 24/7 and prevents cyberattacks by inspecting all incoming and outgoing network data. Most web traffic today is encrypted with HTTPS, so if attackers can sniff the data or use packet sniffing, they will only see a string of undecipherable scrambled characters. SWGs use a unique process called SSL/TLS decryption to scan the encrypted data for malicious code, which is then blocked if found. Some SWG solutions also provide application-level controls to prevent the use of specific software programs. This enables IT administrators to create granular policies based on users, groups, or machines to identify and control the usage of various apps and widgets. It also helps prevent the spread of viruses, worms, and other malicious programs. This feature is often a must-have for organizations to secure their data and protect their users.
Access Control
As organizations move to a flexible working environment, employees must work from anywhere, on any device. This flexibility opens up new attack vectors undermining an organization’s security posture. Legacy secure web gateway solutions can only keep pace with these changing threats if they require more time-consuming upgrades. These updates can be costly and difficult to manage, leading short-staffed IT teams to postpone or skip them. This leaves the door open for attackers to exploit vulnerabilities and exploit employee negligence that leads to data loss and breaches. Next-generation SWG solutions take a holistic approach to security and can mitigate these evolving threats. They integrate with other security solutions in the ecosystem and extend them across organizational environments. SWGs inspect inline traffic, preventing malware from entering the network or accessing sensitive information. They also enable organizations to categorize data and enforce policies for compliance with regulations. Prioritization is another feature that helps organizations to ensure that business-critical applications receive the highest priority.
Policy Enforcement
More than just a filter, an SWG solution constantly monitors web-based activity to understand better threats that other security solutions may not have seen. This helps organizations gain greater visibility into how attackers might target them and improve their overall security posture. To determine policy disposition, SWGs inspect and categorize web traffic based on various attributes, including URL categories. This granularity provides better compliance enforcement to ensure compliance with regulations. A modern SWG solution offers advanced features like content inspection and sandboxing to provide superior threat detection. This includes decrypting encrypted traffic, enabling a deeper look into the contents of web uploads, and blocking unauthorized data exfiltration. It also integrates with security monitoring systems to notify administrators of any problems before an attack occurs. This reduces admin overhead and makes the solution easier to manage for enterprise-wide implementation. This is essential since more employees often work remotely on their devices and connect through untrusted public networks.
Monitoring
With employees working from remote locations and using cloud apps to collaborate, a secure gateway is critical for keeping cyber threats out of the company network. SWGs monitor incoming and outgoing data from all devices to ensure compliance with the policies set by the administrator. Incoming web traffic is scanned for malicious code and URLs, and outgoing data is inspected to ensure sensitive information does not leave the network. This can include credit card numbers, patient medical records, intellectual property, and more. The gateway can also use sandboxing to identify and prevent malware by executing potentially dangerous code in a controlled environment, away from the system. Often, this is the only way to determine if a piece of code is malicious and can be stopped in its tracks. SWGs can also decrypt SSL/TLS session data and inspect it for potential malware or a breach of privacy. They can then log the results for administrators to review. These logs can help to track and alert if a violation has occurred so that steps can be taken to correct the issue.